来源:Tom's Hardware
原英文标题:《Intel Alder Lake, ARM CPUs Affected by New Spectre Vulnerability》

VUSec security research group and Intel on Tuesday disclosed a yet another Spectre-class speculative execution vulnerability called branch history injection (BHI). The new exploit affects all of Intel processors released in the recent years, including the latest Alder Lake CPUs, and select Arm cores. By contrast, AMD's chips are believed to be unaffected.
VUSec安全研究小组和英特尔周二披露了另一个Spectre型推测执行漏洞,称为分支历史注入(branch history injection / BHI)。新的漏洞利用影响了近年来发布的所有英特尔处理器,包括最新的Alder Lake CPU和部分Arm内核。相比之下,AMD的芯片被认为不受影响。
——
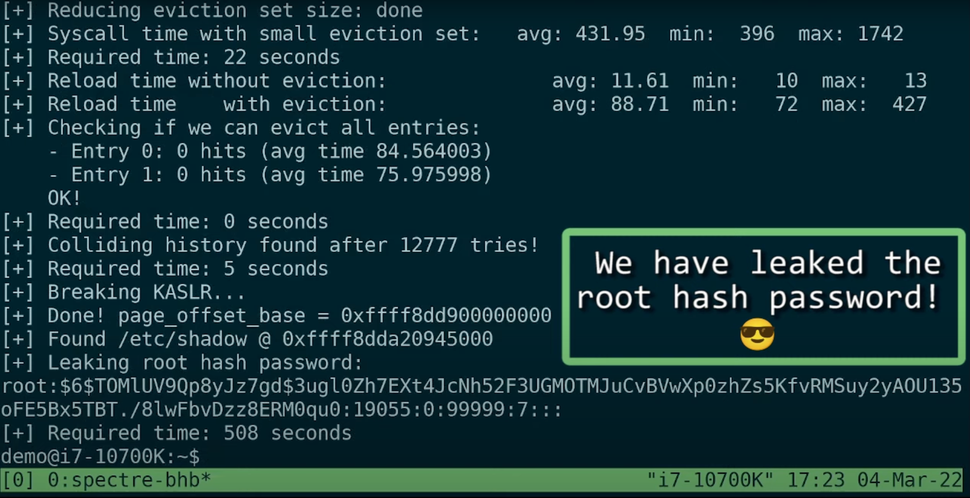
BHI is a proof-of-concept attack that affects CPUs already vulnerable to Spectre V2 exploits, but with all kinds of mitigations already in place. The new exploit bypasses Intel's eIBRS and Arm's CSV2 mitigations, reports Phoronix. BHI re-enables cross-privilege Spectre-v2 exploits, allows kernel-to-kernel (so-called intra-mode BTI) exploits, and allows perpetrators to inject predictor entries into the global branch prediction history to make kernel leak data, reports VUSec. As a result, arbitrary kernel memory on select CPUs can be leaked and potentially reveal confidential information, including passwords. An example of how such a leak can happen was published here.
BHI是一种概念验证攻击,它影响已经容易受到Spectre V2攻击的CPU,但已经采取了各种缓解措施。据Phoronix报道,新的漏洞利用绕过了英特尔的eIBRS和Arm的CSV2缓解措施。VUSec报告称BHI重新启用跨特权Spectre-v2漏洞,允许内核到内核(所谓的内部模式BTI)漏洞利用,并允许犯罪者将预测器条目注入全局分支预测历史记录以生成内核泄漏数据。因此,特定 CPU 上的任意内核内存可能会泄露,并可能泄露机密信息,包括密码。这个链接发布了此类泄漏如何发生的示例。
All of Intel's processors beginning with Haswell (launched in 2013) and extending to the latest Ice Lake-SP and Alder Lake are affected by the vulnerability, but Intel is about to release a software patch that will mitigate the issue.
从Haswell(2013年推出)开始并扩展到最新的Ice Lake-SP和Alder Lake的所有英特尔处理器都受到该漏洞的影响,但英特尔即将发布一个软件补丁,以缓解这个问题。
——
Numerous cores from Arm, including Cortex A15, A57, A72 as well as Neoverse V1, N1, and N2 are also affected. Arm is expected to release software mitigations for its cores. What is unclear is whether custom versions of these cores (e.g., select cores from Qualcomm) are also affected and when the potential security holes will be covered.
Arm的许多核心,包括Cortex A15,A57,A72以及Neoverse V1,N1和N2也受到影响。预计Arm将为其核心发布软件缓解措施。目前尚不清楚的是,这些内核的定制版本(例如,来自高通公司的修改版内核)是否也会受到影响,以及何时会覆盖潜在的安全漏洞。
——
Since this is a proof-of-concept vulnerability and it is being mitigated by Intel and Arm, it should not be able to be used to attack a client or server machine — as long as all the latest patches are installed. There's no indication how much the mitigations will impact performance.
由于这是一个概念验证漏洞,并且英特尔和 Arm 正在缓解该漏洞,因此只要安装了所有最新的补丁,它就不应该被用来攻击客户端或服务器计算机。没有迹象表明缓解措施会对性能产生多大影响。 |
 310112100042806
310112100042806
