来源:Tom's Hardware
原英文标题:《Intel Finds Bug in AMD's Spectre Mitigation, AMD Issues Fix》
News of a fresh Spectre BHB vulnerability that only impacts Intel and Arm processors emerged this week, but Intel's research around these new attack vectors unearthed another issue: One of the patches that AMD has used to fix the Spectre vulnerabilities has been broken since 2018. Intel's security team, STORM, found the issue with AMD's mitigation. In response, AMD has issued a security bulletin and updated its guidance to recommend using an alternative method to mitigate the Spectre vulnerabilities, thus repairing the issue anew.
本周出现了一个新的Spectre BHB漏洞的消息,该漏洞仅影响英特尔和Arm处理器,但英特尔围绕这些新攻击媒介的研究发现了另一个问题:AMD用于修复Spectre漏洞的补丁之一自2018年以来已被破坏。英特尔的STORM安全团队发现了AMD缓解措施的问题。作为回应,AMD 发布了安全公告并更新了其指南,建议使用替代方法来缓解 Spectre 漏洞,从而重新修复问题。
——
As a reminder, the Spectre vulnerabilities allow attackers unhindered and undetectable access to information being processed in a CPU through a side-channel attack that can be exploited remotely. Among other things, attackers can steal passwords and encryption keys, thus giving them full access to an impacted system.
提醒一下,Spectre 漏洞允许攻击者通过可远程利用的侧信道攻击不受阻碍且不可检测地访问 CPU 中正在处理的信息。除其他事项外,攻击者可以窃取密码和加密密钥,从而使他们能够完全访问受影响的系统。
——
Intel's research into AMD's Spectre fix begins in a roundabout way — Intel's processors were recently found to still be susceptible to Spectre v2-based attacks via a new Branch History Injection variant, this despite the company's use of the Enhanced Indirect Branch Restricted Speculation (eIBRS) and/or Retpoline mitigations that were thought to prevent further attacks.
英特尔对AMD的Spectre修复程序的研究以迂回的方式开始 - 英特尔的处理器最近被发现仍然容易受到基于Spectre v2的攻击,通过新的分支历史注入变体,尽管该公司使用了增强型间接分支限制推测(eIBRS)和/或Retpoline缓解措施,被认为可以防止进一步的攻击。
——
In need of a newer Spectre mitigation approach to patch the far-flung issue, Intel turned to studying alternative mitigation techniques. There are several other options, but all entail varying levels of performance tradeoffs. Intel says its ecosystem partners asked the company to consider using AMD's LFENCE/JMP technique. The "LFENCE/JMP" mitigation is a Retpoline alternative commonly referred to as "AMD's Retpoline."
由于需要一种更新的 Spectre 缓解方法来修补这个遥远的问题,英特尔转向研究替代缓解技术。还有其他几个选项,但都需要不同级别的性能权衡。英特尔表示,其生态系统合作伙伴要求该公司考虑使用AMD的LFENCE/JMP技术。"LFENCE/JMP"缓解措施是一种Retpoline的替代品,通常被称为"AMD的Retpoline"。
——
As a result of Intel's investigation, the company discovered that the mitigation AMD has used since 2018 to patch the Spectre vulnerabilities isn't sufficient — the chips are still vulnerable. The issue impacts nearly every modern AMD processor spanning almost the entire Ryzen family for desktop PCs and laptops (second-gen to current-gen) and the EPYC family of datacenter chips.
作为英特尔调查的结果,该公司发现AMD自2018年以来用于修补Spectre漏洞的缓解措施是不够的 - 芯片仍然容易受到攻击。这个问题几乎影响了所有现代AMD处理器,几乎跨越了整个Ryzen系列,用于台式PC和笔记本电脑(第二代到当前一代)以及EPYC系列数据中心芯片。
——
The abstract of the paper, titled "You Cannot Always Win the Race: Analyzing the LFENCE/JMP Mitigation for Branch Target Injection," lists three Intel authors that hail from Intel's STORM security team: Alyssa Milburn, Ke Sun, and Henrique Kawakami. The abstract sums up the bug the researchers found pretty succinctly:
这篇题为《你不能总是赢得比赛:分析分支目标注入的LFENCE/JMP缓解措施》的论文摘要列出了来自英特尔STORM安全团队的三位英特尔作者:Alyssa Milburn,Ke Sun和Henrique Kawakami。摘要非常简洁地总结了研究人员发现的错误:"
——
"LFENCE/JMP is an existing software mitigation option for Branch Target Injection (BTI) and similar transient execution attacks stemming from indirect branch predictions, which is commonly used on AMD processors. However, the effectiveness of this mitigation can be compromised by the inherent race condition between the speculative execution of the predicted target and the architectural resolution of the intended target, since this can create a window in which code can still be transiently executed. This work investigates the potential sources of latency that may contribute to such a speculation window. We show that an attacker can "win the race", and thus that this window can still be sufficient to allow exploitation of BTI-style attacks on a variety of different x86 CPUs, despite the presence of the LFENCE/JMP mitigation."
LFENCE/JMP是分支目标注入(BTI)和间接分支预测引起的类似瞬态执行攻击的现有软件缓解选项,通常用于AMD处理器。但是,此缓解措施的有效性可能会受到预测目标的推测执行与预期目标的体系结构解析之间的固有争用条件的影响,因为这会创建一个窗口,在该窗口中仍可以暂时执行代码。这项工作调查了可能导致这种推测窗口的潜在延迟来源。我们表明,攻击者可以"赢得比赛",因此尽管存在 LFENCE/JMP 缓解措施,但此窗口仍足以允许在各种不同的 x86 CPU 上利用 BTI 风格的攻击。
——
Intel's strategic offensive research and mitigation group (STORM) is an elite team of hackers that attempts to hack Intel's own chips, which you can read about more here.
英特尔的战略进攻研究和缓解小组(STORM)是一个黑客精英团队,试图入侵英特尔自己的芯片,您可以在此处阅读更多相关信息。
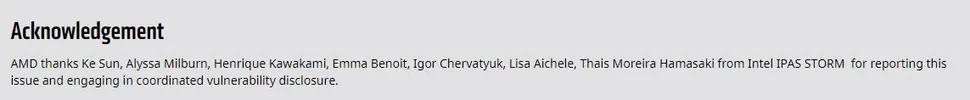
In response to the STORM team's discovery and paper, AMD issued a security bulletin (AMD-SB-1026) that states it isn't aware of any currently active exploits using the method described in the paper. AMD also instructs its customers to switch to using "one of the other published mitigations (V2-1 aka ‘generic retpoline’ or V2-4 aka ‘IBRS’)." The company also published updated Spectre mitigation guidance reflecting those changes [PDF].
作为对 STORM 团队的发现和论文的回应,AMD 发布了一份安全公告 (AMD-SB-1026),声明它不知道使用论文中描述的方法存在任何当前活跃的漏洞利用。AMD还指示其客户切换到使用"其他已发布的缓解措施之一(V2-1又名'通用retpoline'或V2-4,又名'IBRS')"。该公司还发布了更新的Spectre缓解指南,反映了这些变化。
——
AMD commented on the matter to Tom's Hardware, saying, "At AMD, product security is a top priority and we take security threats seriously. AMD follows coordinated vulnerability disclosure practices within the ecosystem, including Intel, and seeks to respond quickly and appropriately to reported issues. For the mentioned CVE, we followed our process by coordinating with the ecosystem and publishing our resulting guidance on our product security website."
AMD向Tom's Hardware评论了此事,他说:“在AMD,产品安全是重中之重,我们认真对待安全威胁。AMD 遵循包括英特尔在内的生态系统内协调的漏洞披露实践,并寻求对报告的问题做出快速、适当的响应。对于上述 CVE,我们遵循了我们的流程,与生态系统协调,并在我们的产品安全网站上发布了我们最终的指南。”
——
We asked Intel if it had found other vulnerabilities in AMD's processors in the past, or if this were an isolated event. "We invest extensively in vulnerability management and offensive security research for the continuous improvement of our products. We also work to get outside perspectives, collaborating with researchers and leading academic institutions to find and address vulnerabilities," a company representative responded. "If we identify an issue that we believe may impact the broader industry, we follow coordinated vulnerability disclosure practices to report potential vulnerabilities to vendors and release findings and mitigations together."
我们询问英特尔过去是否在AMD的处理器中发现了其他漏洞,或者这是否是一个孤立的事件。"我们在漏洞管理和进攻性安全研究方面进行了大量投资,以持续改进我们的产品。我们还努力获得外部观点,与研究人员和领先的学术机构合作,以发现和解决漏洞,"一位公司代表回应道。"如果我们发现我们认为可能会影响更广泛行业的问题,我们会遵循协调的漏洞披露实践,向供应商报告潜在的漏洞,并一起发布调查结果和缓解措施。
——
Security vulnerabilities obviously make for what would normally be strange bedfellows. In this case, that's a good thing: The Spectre vulnerabilities threaten the very foundations of security in the silicon that powers the world. AMD's security bulletin thanks Intel's STORM team by name and noted it engaged in the coordinated vulnerability disclosure, thus allowing AMD enough time to address the issue before making it known to the public. That's good for everyone.
安全漏洞显然会成为通常很奇怪的床伴。在这种情况下,这是一件好事:Spectre漏洞威胁到为世界提供动力的芯片中的安全基础。AMD的安全公告点名感谢英特尔的STORM团队,并指出它参与了协调的漏洞披露,从而使AMD有足够的时间在向公众公布之前解决问题。这对每个人都有好处。 |
 310112100042806
310112100042806
